My last post, a guide on disclosing Linux kernel vulns, might have been a bit of a giveaway, but recently I discovered a vulnerability in the Linux kernel that's been lurking there since 4.8 (July 2016)!
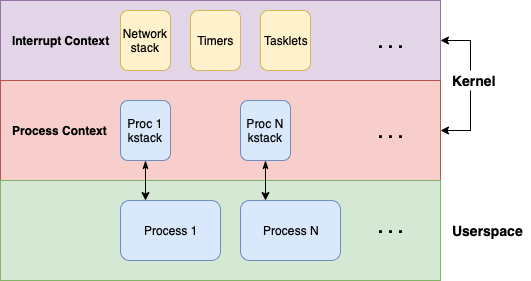
Now that the embargo is up, I can share it with the world! CVE-2022-0435 is a remotely and locally exploitable stack overflow in the TIPC networking module of the Linux kernel (don't worry, if you haven't heard of TIPC, it probably isn't loaded by default on your distro).
Find Out More
If you want a brief technical overview of the vulnerability, check out the advisory I posted to the oss-security mailing list:

For a more detailed analysis of the vulnerability, covering the same content as the advisory, check out my blog post over on the Immunity blog:
Focusing more on exploitation, I discuss the work and techniques involved in writing a contemporary remote kernel exploit, using CVE-2022-0435 as a case-study:
Get in Touch!
General reminder that if you have any questions / corrections / suggestions / request for content, regarding CVE-2022-0435 or any of my Linuxy security-y stuff, feel free to @ me on Twitter!
exit(0);